Lucian Constantin’s recent article “Expect more cyber-espionage, sophisticated malware in ’12, experts say” states that cyber-attacks in 2012 will increase with more sophisticated malware. Certainly companies like MicroTrend, Symantec and others have their work cut out for them to eradicate these attacks once they are launched. But taking a step back, the question arises as to how malware is first getting into the networks.
Answer: employee’s carelessness.
Using social engineering attacks are still the best and cheapest way to distribute malware. Spam emails, phishing, spearfishing, etc., all utilize attachments that can hide the malware. It still is amazing that such an and old and simple method is still the most effective. An according to some experts, educating the employees about information security is a waste of time. I disagree since even if one person is helping by being educated and aware it is better than having none. But education alone is not the solution.
Technology applications, networks and operating systems have to incorporate security as one of their key design components. Stop the patching and all the backward compatibility design concerns and start create an entirely new OS from scratch. We don’t run DOS and Windows 98 anymore.
Software applications also need to incorporate high security standards like integration with multi-factor credentials. Using a smartcard that first authenticates the user to the card, then the card to the computer, then authenticates the card and server to each other, and finishes up with the user to the application can greatly improve a company’s security.
Public cloud services are still scary at best. Do you really know how and where your data is being stored? Plus, when some of the biggest public cloud companies are “sidestepping security” with protection clauses in their contracts should tell you something. Private clouds can have more security safeguards but it requires knowledgeable people to build and manage.
Security is only as strong as the weakest link and that link is the employee. I would wager that majority of the employee caused breaches are done through carelessness. Employees have to get their jobs done and will often circumvent security protocols so as to increase convenience and efficiencies. That is why any security plan has to take into account the user. Otherwise, corporate officers are lulled into a false sense of security. A 25-character random password that has to be changed every 7 days is super security but don’t be surprised when there is an increase in Post-it Note supplies because these passwords simply cannot be memorized by most employees.
Power LogOn® by Access Smart® has been delivering multi-factor authentication, smartcard-based password management solutions for years. Users are able to store multiple passwords on a single smart card, no passwords are ever stored with in a computer that others can access our hack, and when the card is removed from the computer no critical logon data is left behind on the computer. If the card is lost or stolen all the passwords are protect because the card authentication includes a limited number of false entries before it is locked and needs IT assistance. From the users perspective a lost card is easily recoverable without having to change all your passwords.
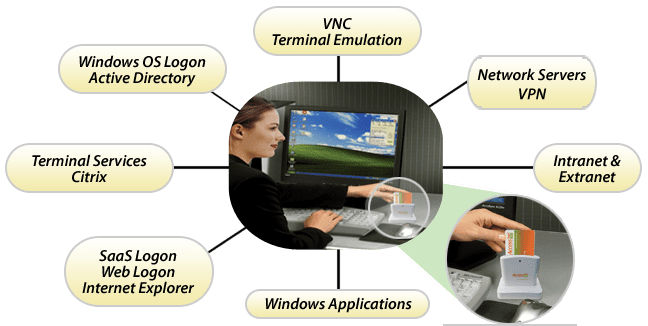
Users passwords need to be de-centralized and always in the possession of the user. Power LogOn is being used by individuals, small businesses, and large enterprises. So don’t wait for Windows 8 to think you can securely manage your passwords. Implement today and protect your data. Complex passwords are recognized as the way to secure accounts. Power LogOn allows businesses to securely manage all those passwords and for IT to be put back in control of logon security.


