Silo cybersecurity creates “vulnerability gaps” which hackers exploit
How many cybersecurity news articles and blogs have you read about how IT Managers can prevent a cyber-attack on their company’s network? One author promotes Multi-Factor Authentication (MFA) as the solution. Another author says that a strong password manager is required. Finally, the third author emphasizes the need for data encryption.
Way too often, networks are designed with multi-factor authentication, password management and data encryption treated as three separate cybersecurity components (or silos). Each piece gets installed at different times and in different orders of priority. The problem with silo security is that it creates “vulnerability gaps” between the products which hackers exploit.
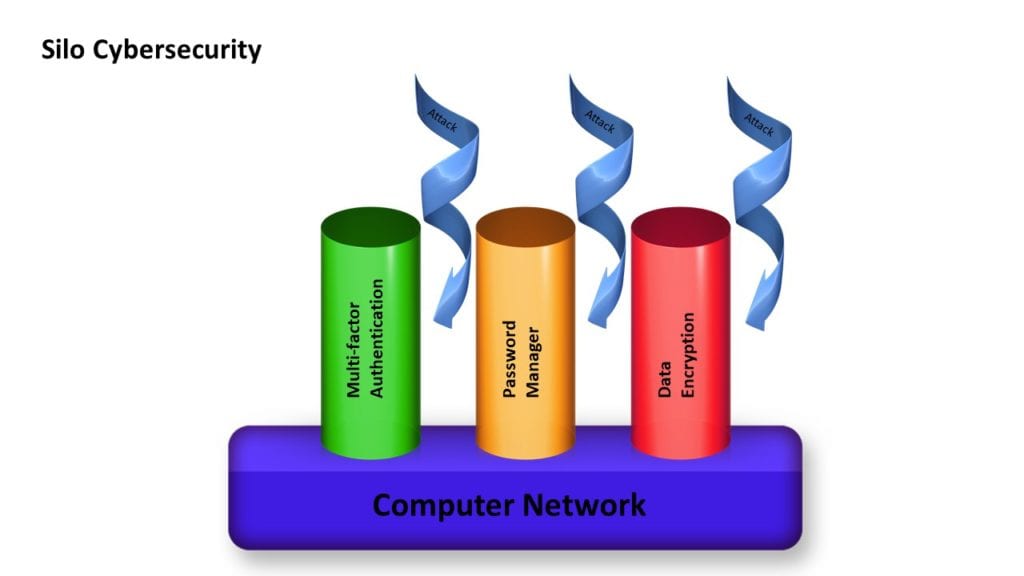
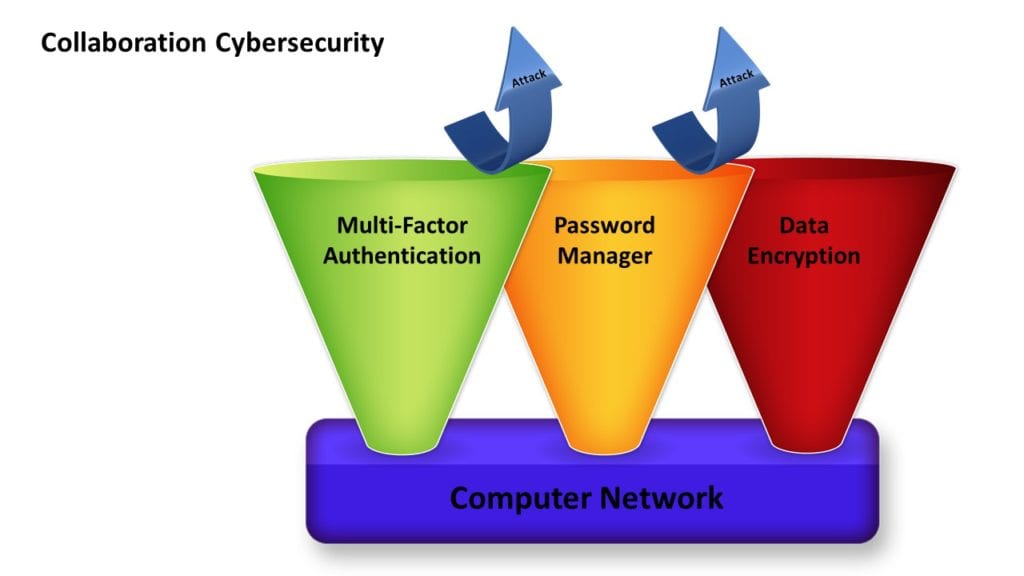
All three are needed and must be integrated together. MFA does little good if the user still creates weak passwords. All that creates is the IT Administrator knowing that Bob uses “123456” to unlock his computer.
A password manager might allow for the creation and storage of complex and unique passwords, but that is useless if there is no way to know who is accessing the passwords. Bob’s daughter playing around on his computer might think it’s fun to access all his company’s files and applications with a single mouse click.
Similarly, data encryption programs can be rendered useless if the logon credential is easily compromised and you don’t know who is accessing it. If there is a password on a sticky note by your computer, the company’s custodian could easily use it to send confidential files to unauthorized people.
The Power LogOn plus data encryption cybersecurity solution combines very strong MFA (built around the employee ID badge) with an enterprise password manager. Now your customer’s IT administrator knows with certainty that Bob, and only Bob, is connecting to the network and that Bob is authorized to access the application.
With all the new cybersecurity legislation and best practices being published by the government agency NIST, IT must authenticate who is launching an application, and authorize what data the user can access and modify. To add this level of security to your application, Power LogOn’s API code can be requested to add very strong authentication to your application without you having to develop it yourself.


